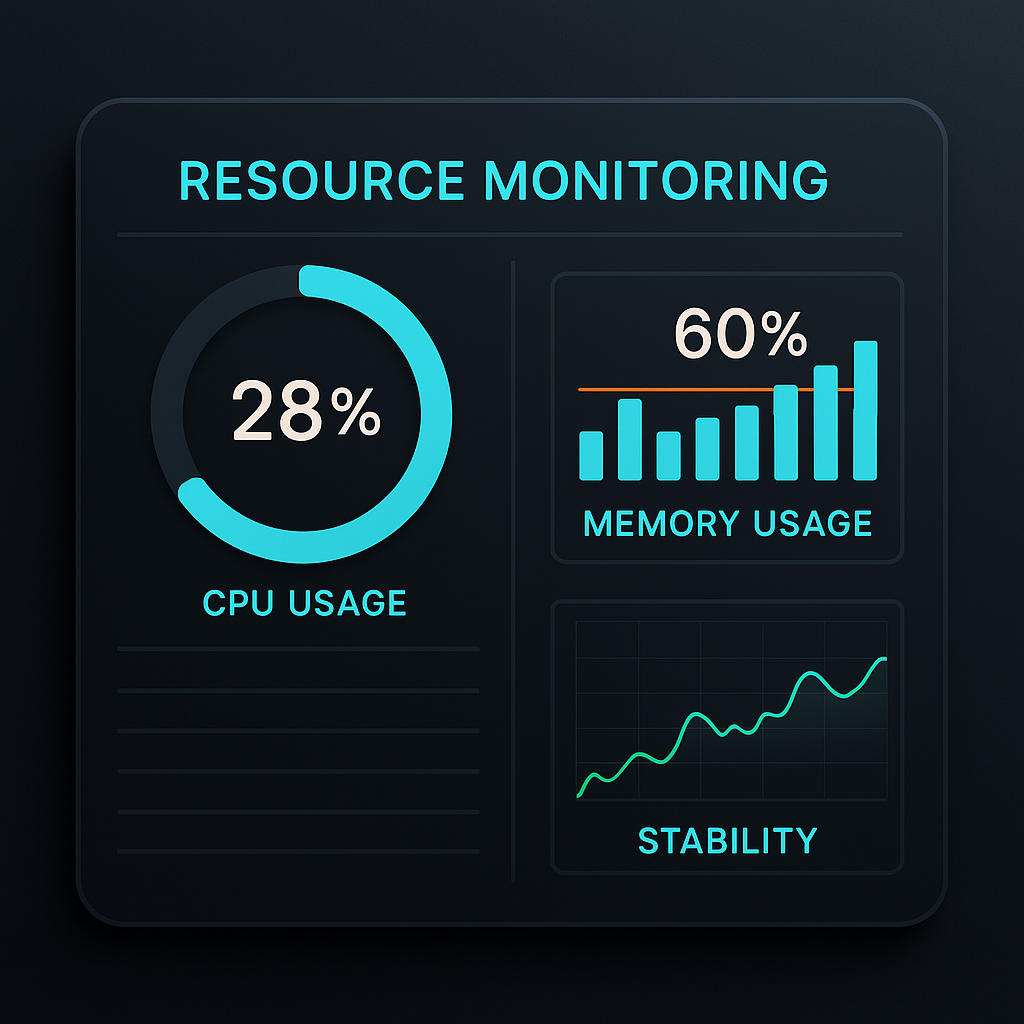
Proxy Ressource Footprint
When it comes to honeypots in the embedded—especially automotive—domain, the proxy-based approach used by the CROWSI framework comes with clear advantages. By shifting the actual honeypot to an isolated backend infrastructure and exposing it through a lightweight proxy on the edge device, we minimize both risk and resource demand at the edge. Of course, the … Read more