Honeypot Solution for Edge Devices
CROWSI is a backend based open-source honeypot platform, tailor made to protect edge device scenarios.
It is built to provide early notifications of malicious activities as well as valuable insights while luring attackers away from actual assets.
Let‘s build a world where every attack ends in a decoy trap!
What is a Honeypot?

Honeypots are decoy systems that are intended to be attacked. They mimic actual vulnerable systems, by this attracting attackers around your eco-system and luring them away from actual assets.
Read more in our blog post.
Why to use Honeypots?
Early Notifications
Creates Insights
Binds Resources
Honeypots divert attackers’ limited resources by engaging them with decoy systems, reducing their ability to target real assets and providing protection by wasting their time and efforts.
Read more in our blog post.
CROWSI Overview
CROWSI is a Kubernetes based platform that can orchestrate and expose containerized honeypot applications. It allows you to add whatever application container that suits your scenario, while serving as default a low interaction container application that implements a HTTP server, logging details of incoming requests.
By integrating CROWSI into your edge device via another reverse proxy on it, it allows you to mimic a badly protected app on your edge device or your backend to attackers.
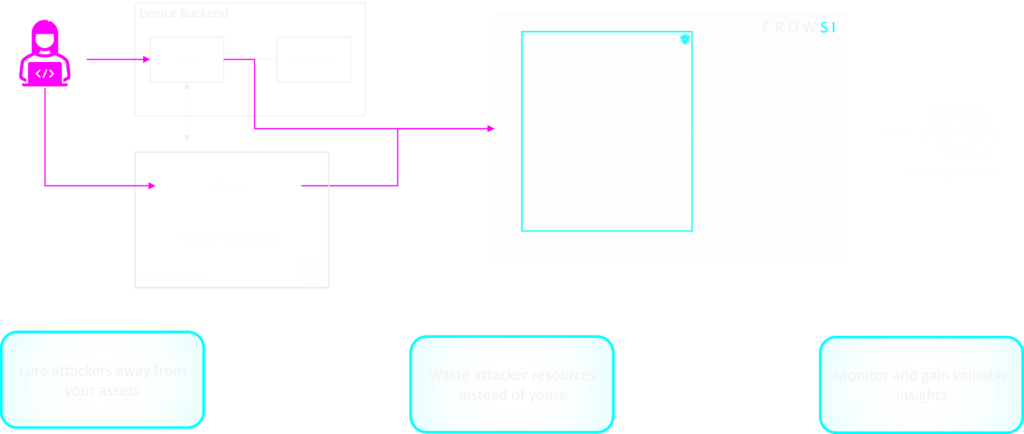
Whenever an attacker targets the edge device and starts interacting with the open port of the proxy, all his requests shall be forwarded to CROWSI, where the requests and activities will be logged in detail. Furthermore, via this forwarding we achieve the positive effect of shifting the main risks of vulnerable decoys to an isolated backend instead of incorporating them into your assets.
To learn more, read our documentation or browse the source code on GitHub. Also make sure to check out our following demo video!
Demo
Why using CROWSI to protect your vehicle fleet?
Although suitable to protect any edge device scenario, CROWSI was originally developed to provide an easy and effective mean to enable propper vehicle security monitoring as required e.g. by the UN – R 155.
Check out our article on the big challenge of vehicle security monitoring and how CROWSI can help in this domain.


Professional Services
You don’t want to spend valuable internal resources on deploying and operating CROWSI on your own?
You need support or customization?
You are looking for additional high-interaction honeypot decoys?
Check out our professional service offerings.
