At CROWSI, we believe that honeypots are a valuable tool in addressing the significant challenge of vehicle security, particularly in the realm of vehicle security monitoring as part of secure vehicle operations.
In our first blog post, we discussed why honeypots are beneficial for automotive security. In our previous blog post, we explored different design options, beginning with in-vehicle honeypot decoys.
In this blog post, we now want to delve into the second design option: cloud-based automotive honeypots that simulate vehicle assets, with a focus on the challenge of maintaining their credibility.
Why Publicly Exposed Vehicle Assets Are Not Credible
As discussed in our previous blog post, integrating system decoys directly into vehicles presents challenges related to cost and risk. As an alternative, some propose simulating a vehicle ECU (e.g., a connectivity ECU) or even an entire vehicle in a cloud environment and exposing it to the public internet.
We believe this idea often originates from attack scenarios like the well-known Jeep Hack back in 2015. In that case, researchers were able to connect remotely to a vehicle over the public mobile network due to inadequate network restrictions. We recommend reviewing their research paper for further details.
Using this attack model as a basis, one could imagine simulating a connected vehicle ECU on a cloud server, exposing it to the public internet, and monitoring for malicious interactions. While this setup would likely attract attacks, they would mostly come from opportunistic attackers rather than those specifically targeting automotive systems.
Since the Jeep Hack and similar incidents, OEMs as well as network providers take great care to ensure that valuable assets are not exposed in larger public networks. Consequently, professional attackers would quickly recognize such a widely accessible system as a honeypot decoy, rendering it ineffective.
This raises an important question: How can a credible cloud-based honeypot be designed using offboard resources?
Designing Credible Systems
The research paper “Work-in-Progress: Emerging E/E-Architectures as Enabler for Automotive Honeypots” by Niclas Ilg, Dominik Germek, Paul Duplys, and Michael Menth provides an insightful discussion on designing credible vehicle honeypots on the internet.
The key takeaway is that automotive honeypots should be placed behind real or simulated OEM web services. This aligns with recent attack trends, where threats increasingly target backend services associated with vehicle assets rather than the vehicles themselves.
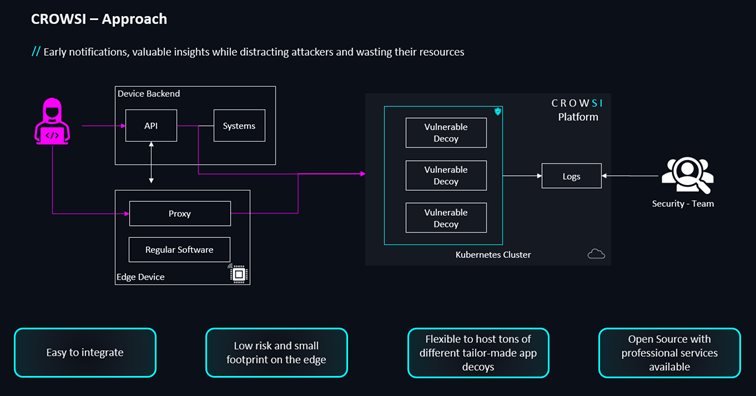
At CROWSI, we also think that this is a very promising approach because it aligns with real-world attack patterns, making it more effective in deceiving attackers. By placing honeypots behind realistic attack vectors, we increase their credibility and likelihood of capturing meaningful threat intelligence. That’s why we suggest to not only expose your decoys hosted on CROWSI within your actual vehicle but also expose suitable decoys within the web services of your backend.
Conclusion
Designing credible cloud-based automotive honeypots that simulate vehicle assets is challenging but achievable. As discussed, strategically placing honeypots behind realistic attack vectors increases their credibility and effectiveness.
With CROWSI, you have the opportunity to implement both in-vehicle and cloud-based honeypots within a single platform.
We’d love to support your automotive honeypot journey. Try CROWSI today and see how our platform can help you implement effective in-vehicle and cloud-based honeypots! Share your thoughts and experiences with us—we’re eager to collaborate and learn together! Reach out to us and let’s build a world where attackers can never be sure whether they’re interacting with a real asset!

